November 2023

Your monthly readout of the Australia and New Zealand cyber threat environment from the desk of CyberCX Intelligence. Cyber Adviser cuts through the noise – delivering you insights and expert analysis in 5 minutes or less.
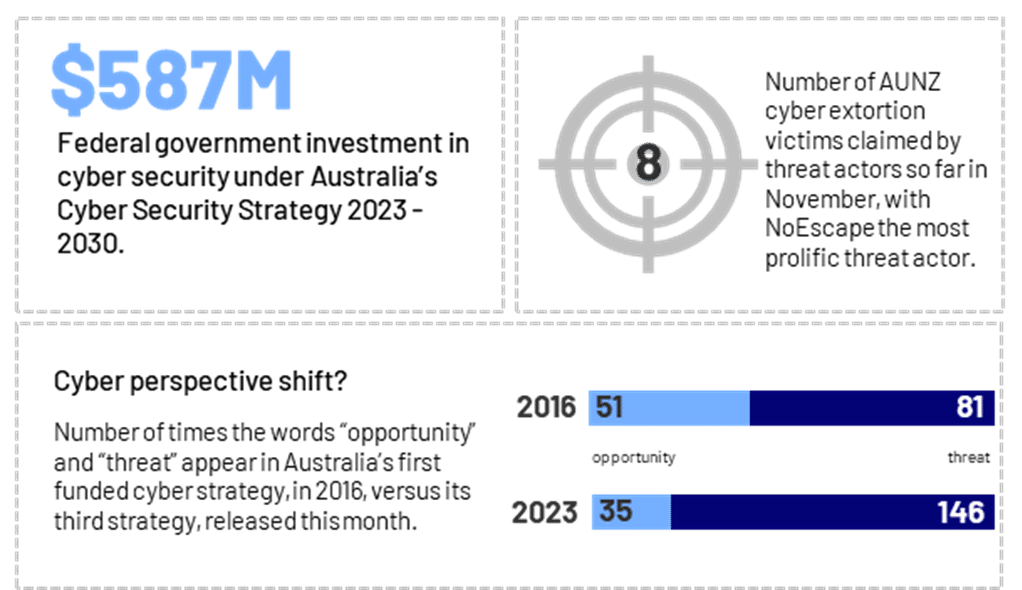
By the numbers
Case files
23andMe data breach: Where do ideologically-motivated threat actors feature in your threat model?
In October, a threat actor calling itself “Golem” leaked samples of personal information it claimed to have stolen from 23andMe on the notorious cyber crime forum, BreachForums. 23andMe, a genetic testing service, later confirmed it had suffered a data breach due to large-scale “credential stuffing” attacks against users on its website. Initially, Golem released 1 million lines of data allegedly relating to customers with Ashkenazi Jewish heritage. Then, on 4 October, Golem began offering accounts for sale for US $1-$10 each and offered to accommodate special requests including filtering for specific ethnicities, locations and phenotypes. Based on the leaked data and Golem’s anti-Israel commentary, we assess the attack was at least in part ideologically motivated.
So what? As geopolitics becomes more febrile, this incident is a reminder to consider ideologically-motivated criminals in your organisation’s threat model – and the threat they pose to vulnerable individuals or groups in your datasets. We’re also seeing more threat actors use credential stuffing to scrape large datasets – multi-factor authentication can help prevent this.
Non-profit: Cyber attack disconnects telemarketer
In late October, Brisbane-based telemarketing organisation Pareto Phone ceased operations, after suffering a widely publicised cyber incident. Pareto Phone provided telemarketing and donation collection services for more than 70 Australian and New Zealand charities and non-profit organisations. In late July, Pareto Phone was listed on the dark web leak site of prolific cyber extortion group LockBit. LockBit subsequently released stolen data, including personal information and financial records, relating to at least 50,000 donors. Some of the stolen records were over 15 years old. The Australian Information Commissioner is investigating possible breaches of Australian privacy laws linked to the incident.
So what? This is one of the most visible examples of an Australian business ceasing operations as the direct result of a cyber attack. As the regulatory environment around data breaches and privacy tightens, and consumer and market expectations continue to change, organisations should ensure they have appropriately quantified the impacts of a major cyber incident for their business.
The rising insider risk: Could a cyber criminal be trying to hire your staff?
In October, cyber extortion group Everest posted an ad to their dark web dedicated leak site, inviting employees in the US, Canada and Europe to provide access to their corporate network. In return, Everest offered a “good percentage” of the attack’s profits. Previously, cyber criminals have typically approached employees directly, via email or direct message, or posted ads on cyber criminal forums. These approaches are often facilitated by social media networks, like LinkedIn, which threat actors use to construct an organisational chart of their target. It’s less common to see an invitation at-large on a threat actor’s dedicated leak site.
So what? CyberCX Intelligence is aware that cyber criminals are actively recruiting employees to gain initial access to victim networks. Everest’s ad is just the latest development in a worsening trend. The risk posed by malicious insiders can be mitigated by adopting zero-trust and least-privilege security architectures and implementing personnel security that includes ongoing monitoring.
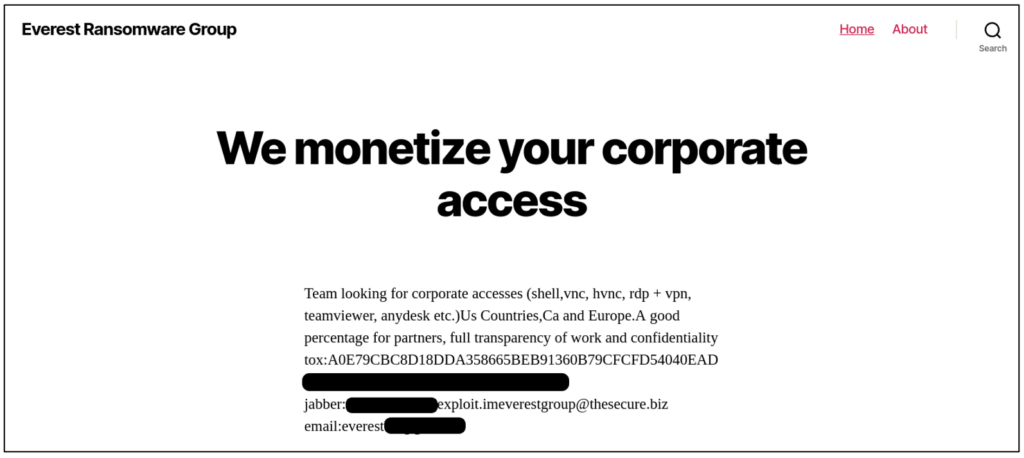
Source: Everest dark web leak site, November 28
Environment scanning
Last week, the Government released its long-awaited Cyber Security Strategy 2023-2030. Here are our five favourite measures and the threat intelligence insights they reflect.
| Measure | Intelligence insight | |
 |
A new Small Business Cyber Security Support Service. | In our 2023 Ransomware and Cyber Extortion Best Practice Guide, we noted we’ve seen more cyber extortion attacks against small businesses. |
 |
A no-fault, no-liability ransomware reporting obligation for business. | We know that cyber crime is systematically underreported. This measure will help build a better threat intelligence picture. |
 |
A new pilot ISAC for threat sharing across the health sector. | Healthcare is essential to our communities, but consistently in the top 5 sectors we see targeted by cyber extortion criminals. |
 |
Reform to clarify managed service providers’ cyber security obligations. | Managed service providers are high-value targets for cyber criminals and nation-states, with a number of high profile incidents affecting the sector – and thousands of its downstream customers – globally and in Australia. |
 |
A process to identify and protect datasets of national significance. | Criminals continue to shift towards data theft extortion and nation-state actors continue to demonstrate a voracious appetite for personal, commercial and strategic information, two trends that may be exacerbated by the significant role of data in the current wave of AI innovation. |
In case you missed it: Unpacking the Australian Cyber Security Strategy
This week, our Executive Director, Cyber Intelligence joined our Chief Strategy Officer to unpack what the newly released Australian Cyber Security Strategy means for Australian organisations. You can catch-up on demand, here.
About CyberCX Intelligence
CyberCX Intelligence is a uniquely Australia and New Zealand focused capability, with unparalleled visibility into the AUNZ cyber threat landscape. We have the information, access and context to give our partners a decision advantage. Our partners receive:
- Actionable, contextualised intelligence, analysed by experts in AUNZ threat analysis.
- Sector and organisation-specific insights that are relevant and timely.
- High value, low volume artefacts that help their information overload, not add to it.
- A two-way partnership with intelligence designed for your organisation and how you plan to use it.




