October 2023

Your monthly readout of the Australia and New Zealand cyber threat environment from the desk of CyberCX Intelligence. Cyber Adviser cuts through the noise – delivering you insights and expert analysis in 5 minutes or less.
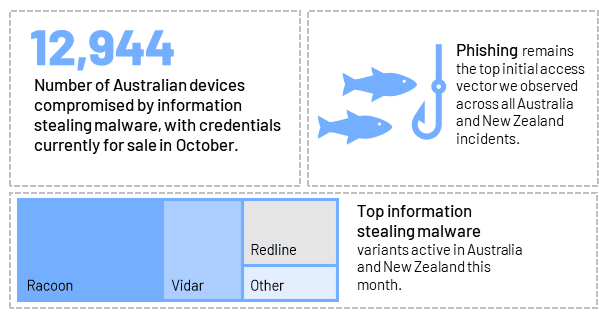
By the numbers
Case files
A Fancy Bear on Only Fans? The rise and rise of info-stealing
An information stealing campaign targeting Australia and loosely linked to a Russian nation-state threat actor may indicate Russia’s continued interest in conducting espionage in the region. In early September, security researchers identified an information stealing campaign, dubbed Steal-It, explicitly targeting countries including Australia, Poland and Belgium. The campaign used OnlyFans phishing lures specifically for Australian targets. Researchers at Zscaler linked this campaign to Russian nation-state actor APT28 (also tracked as Fancy Bear). While the similarities aren’t enough to substantiate a direct attribution, we assess there’s a real chance that an experienced and capable threat actor is behind Steal-It – based on the complexity, persistence and evasiveness of the activity.
So what? This activity’s a reminder of the need to ensure employees’ personal activity and devices are adequately separated from work activity and/or devices.
Hello, it’s me: Could your IT helpdesk be your weakest link?
In last month’s Cyber Adviser, we warned that a focus on data breaches shouldn’t distract us from preparing for the real risk of ransomware. In September, major US entertainment companies, MGM Resorts and Caesars Entertainment, fell victim to Alphv ransomware. Cyber extortion group Scattered Spider reportedly used social engineering techniques against both venues’ IT helpdesk service provider, Okta, to gain access to their networks. Okta’s chief security officer has since confirmed that five Okta clients, including MGM Resorts and Caesars, had been impacted by Scattered Spider attacks involving Alphv ransomware. CyberCX Intelligence is aware of Scattered Spider, as well as other members of the Alphv affiliate program, targeting Australian organisations within the last 12 months. We also assess that Scattered Spider is likely to continue using social engineering techniques that focus on IT help desk providers to secure initial access to their customers’ accounts.
So what? Organisations should ensure their IT help desks are maintaining strict password reset policies with processes to properly verify the identity of any employee calling to request an MFA reset.
Market manipulation: A Kremlin insider and an elaborate hack-to-trade scheme
In September, the US Attorney’s Office sentenced Russian businessman Vladislav Klyushin to nine years’ prison for an elaborate US$93 million hack-to-trade scheme. Between 2018 and 2020, Klyushin and his co-conspirators viewed and downloaded yet-to-be announced earnings reports for hundreds of customers, using the information to trade before the news was public.
Klyushin, described as a “Kremlin insider” by the FBI, was reportedly awarded an Order of Honour by the Russian President in 2020 and owns a Moscow-based IT company, whose customers include multiple Russian government entities, including the President’s office. One of Klyushin’s co-conspirators and M-13 employee is a former Russian intelligence officer who has already been indicted in the US – once for his alleged role in interfering with the 2016 US election “by way of computer hacking”, and also for his alleged role in hacking and disinformation campaigns targeting international anti-doping and sporting entities.
So what? Cyber criminal hack-to-trade operations can be incredibly profitable and – sometimes – hard to detect. Is this activity in your threat model? This case also reminds us of the murky overlap between cyber crime, cyber security companies and intelligence agencies within Russia.
In case you missed it: Dark web exposed webinar
This week, our expert team of cyber investigators took webinar participants on a discovery of the deep and dark web, including demonstrations of how it is used by criminals, the challenges in investigating them and a demonstration of the customised tools CyberCX has developed to assist in investigations we’ve done. If you missed it, you can request a copy of the download link by emailing us at [email protected]
Environment scanning
![]()
In October, the intelligence chiefs from Australia and New Zealand joined their Five Eyes counterparts to warn business leaders about the Chinese government’s “sustained, scaled and sophisticated” theft of IP. Both Australia and New Zealand have to date been judicious about naming-and-shaming foreign governments for malicious cyber activity. Their increased willingness to point the finger indicates their growing concern about the threat.
![]()
In October, the Australian Prime Minister and Microsoft announced a $5 billion investment in Australia, including data centres, skills training and a joint “Cyber Shield” initiative with the Australian Signals Directorate. With the Australian Government’s Cyber Strategy due imminently for release, there are likely to be further announcements in the near term on new industry partnerships and standards.
![]()
In late September, the Australian Government released the exposure draft of Digital ID legislation, a scheme intended to minimise the amount of personal information individuals need to entrust to private industry. As organisations increasingly view personal information as “uranium” (valuable, but potentially toxic to hold or mismanage), a better Digital ID scheme could reduce the impact of future data breaches – for ordinary citizens and the companies that need to verify their identity.
Subscribe to Cyber Adviser
Receive the latest cyber insights and expert analysis, straight to your inbox.
About CyberCX Intelligence
CyberCX Intelligence is a uniquely Australia and New Zealand focused capability, with unparalleled visibility into the AUNZ cyber threat landscape. We have the information, access and context to give our partners a decision advantage. Our partners receive:
- Actionable, contextualised intelligence, analysed by experts in AUNZ threat analysis.
- Sector and organisation-specific insights that are relevant and timely.
- High value, low volume artefacts that help their information overload, not add to it.
- A two-way partnership with intelligence designed for your organisation and how you plan to use it.



