May 2024

Your readout of the Australia and New Zealand cyber threat environment from the desk of CyberCX Intelligence. Cyber Adviser cuts through the noise – delivering you insights and expert analysis in 5 minutes or less.
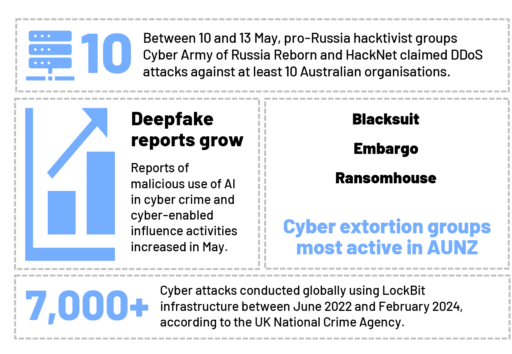
May by the numbers
TOP 2 CYBER INSIGHTS
Spies, interrupted: In April and May, there was a significant uptick in European governments attributing malicious insider activity to foreign intelligence services
What: Across April and May, multiple European nationals were arrested for conducting espionage on behalf of the Chinese and Russian governments. In many cases, the activities had commenced years earlier. These developments are not unique to Europe. In May, it was reported that Australian politicians belonging to the Inter-Parliamentary Alliance of China were targeted by Chinese nation-state actor APT31 in 2021 and 2022.
So what: Both Russia and China are known to recruit and/or embed malicious insiders for espionage and foreign interference purposes. The time lag between malicious intelligence activities taking place and domestic intelligence services notifying victims is noteworthy. Organisations should be vigilant about this type of threat and shouldn’t wait to be notified after the fact.
Rise of the hacktivist: In May, the ideologically motivated actors targeting AUNZ organisations diversified
What: In May, pro-Russian hacktivist groups Cyber Army of Russia Reborn (CARR) and HackNet claimed distributed-denial-of-service (DDoS) attacks against at least 10 Australian organisations. CARR’s targeting of Australian organisations is significant due to its operational technology (OT) targeting capabilities and affiliation with the Russian state. Also in May, a self-proclaimed hacktivist actor claimed defacements of two Australian organisations – a family violence support provider and a private school. We do not yet know this actor’s motivation.
So what: We continue to judge that ideologically motivated activity is unpredictable and can occur with little warning or immediately apparent rationale, meaning that any AUNZ organisation could be a plausible target. Likely impacts to targeted organisations involve temporary disruption to the availability of websites and other internet-exposed services.
Environment scanning
![]()
In late May, the Australian Communications and Media Authority (ACMA) announced legal action against Optus over a 2022 cyber breach. ACMA alleges that Optus failed to protect the confidentiality of personal information of its customers from unauthorised access.
![]()
Global law enforcement revealed the identity of the leader of the LockBit cyber extortion group, LockBitSupp. Despite this, in late April, CyberCX Intelligence observed a surge in alerts relating to LockBit ransomware detection – we assess these incidents mostly relate to leaked LockBit ransomware builders.
![]()
In May, the Australian Parliament passed the Digital ID Bill 2024 and Digital ID (Transitional and Consequential Provisions) Bill 2024, with digital identity legislation to come into effect in November 2024.
Want more insights?
Our intelligence reporting services deliver timely, curated intelligence to your security teams and business leaders. Subscribers receive short reports on cyber threats as they happen and a monthly digest with trend analysis and real-world incident case studies. Learn about new campaigns targeting AUNZ organisations, optimise your controls for latest threat actor tradecraft, and confidently understand the cyber impacts of major geopolitical events and regulatory shifts.
Contact us at [email protected] to discuss how we can design a service tailored to your organisation.
About CyberCX Intelligence
CyberCX Intelligence is a uniquely Australia and New Zealand focused capability, with unparalleled visibility into the AUNZ cyber threat landscape. We have the information, access and context to give our partners a decision advantage. Our partners receive:
- Actionable, contextualised intelligence, analysed by experts in AUNZ threat analysis.
- Sector and organisation-specific insights that are relevant and timely.
- High value, low volume artefacts that help their information overload, not add to it
- A two-way partnership with intelligence designed for your organisation and how you plan to use it.




