August 2023

Your monthly readout of the Australia and New Zealand cyber threat environment from the desk of CyberCX Intelligence. Cyber Adviser cuts through the noise – delivering you insights and expert analysis in 5 minutes or less.
By the numbers
Case files
Keys to many kingdoms: China implicated in another, significant Microsoft supply chain attack
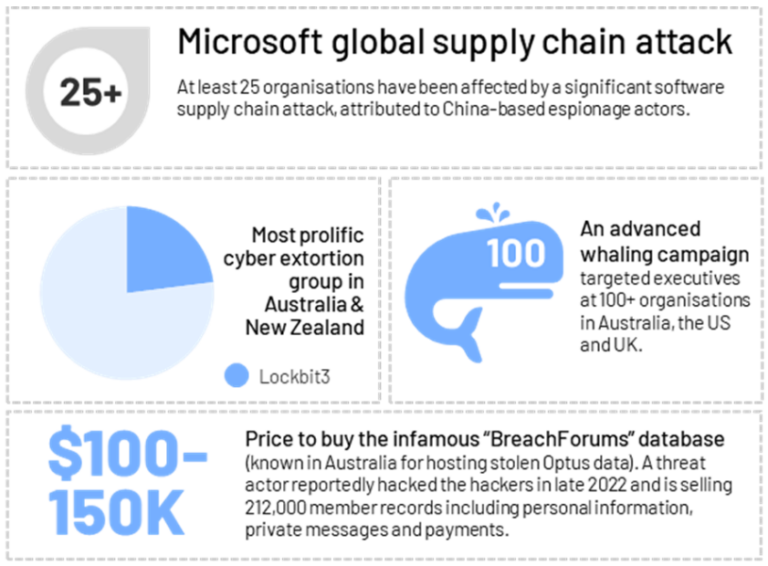
In July, Microsoft disclosed that a China-based espionage actor stole a Microsoft identity/access signing key and used it to craft valid authentication tokens for Outlook. Beginning in May, the threat actor accessed email accounts related to at least 25 organisations.
No Australian or New Zealand organisations have been reported as affected, however most victims have not been publicly identified. Identity/access provider keys are one of the highest value secrets a threat actor can obtain. The US Cybersecurity and Infrastructure Security Agency (CISA) confirmed that data was stolen from at least one US government agency. The impacted agency detected the breach because it had premium logging and a baseline of the applications expected to be accessing mail items. This emphasises the importance of audit logs, but also means it is highly likely that some victims have not detected the intrusion. CyberCX Intelligence assesses that it’s plausible that this campaign extends much wider – and possibly further back in time – than currently known.
Whale of a time: Are your executives resilient to highly targeted spear-phishing?
In early July, CyberCX observed a large-scale whaling campaign impacting executives in at least Australia, the US and the UK. The threat actors used invoice and secure message-themed lures, particularly DocuSign-related lures, to attempt to obtain Microsoft credentials from targets. Based on the distribution of targets, we assess that it is likely that the threat actors were deliberately targeting executives and other high-profile victims.
The threat actors’ link-based phishing chain contained at least two redirects before the primary phishing page, with elements of the redirect chain being unique to each victim. CyberCX identified at least 100 instances of organisations having had a unique redirector URL endpoint generated for an individual employee. Redirections were at least moderately hardened against security tools and attempted to divert or drop inauthentic connections.
We assess that is it highly likely that the threat actors re-pivoted from successful compromises to continue spreading. This technique is likely to be particularly effective when compromised email accounts relate to prominent figures with preexisting relationships.
A bear in there? Pro-Russian hacktivists continue to target Australian and New Zealand organisations
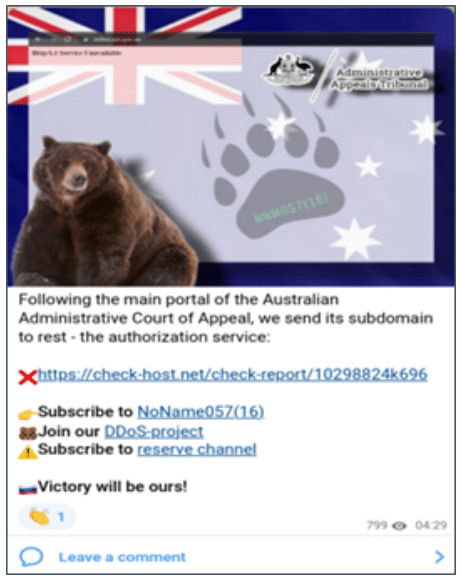
In mid-July, pro-Russia hacktivist group NoName057(16) claimed to have conducted DDoS attacks against the New Zealand Parliament and Law Commission. The claimed attacks followed claimed attacks on the Australian Parliament and the Administrative Appeals Tribunal (AAT) through June and July.
NoName057(16) publicly indicated this campaign was motivated by media coverage of both countries’ support for Ukraine. NoName057(16) used an application-layer DDoS attack to target subdomains of the AAT. Targeting subdomains is likely to be an attempt to disrupt peripheral services that are less hardened against DDoS attacks.
NoName057(16) claims to have impacted subdomain of Administrative Appeals Tribunal, but incorrectly names the organisation as the Administrative Court of Appeal.
Globally, NoName057(16) is a highly active pro-Russia hacktivist group. Despite the campaign being the first instance of it targeting Australian and New Zealand organisations, the attacks have received limited media attention. Like other pro-Russia groups, NoName057(16) favours high-visibility targets and courts publicity.
CyberCX continues to assess high-visibility Australian and New Zealand organisations are a likely target for pro-Russia hacktivists. During periods when Australia and New Zealand are supplying additional military aid to Ukraine, the likelihood of pro-Russia hacktivist targeting temporarily, but significantly, increases. CyberCX continues to recommend that organisations ensure that business-critical public facing systems have appropriate DDoS mitigations in place.
Environment scanning
![]()
APRA has released a new “Operational Risk” prudential standard, specifying that bank, insurer and super boards are “accountable” for oversight of operational risk management. This is another reminder of the increasing regulatory risks organisations – and board members – face when cyber risk is realised.
![]()
The data broker industry is in the government’s sights. The ACCC released an issues paper, noting that despite the “vast amounts of information [data brokers] collect about Australian consumers” there is “little transparency or awareness” about their operations. Across the region, regulators have a growing interest in mapping and protecting personal information.
![]()
Australian parliamentarians raised concerns about the cyber security of the solar energy grid, given the dominance of Chinese-owned companies in the “smart inverter” market. This is just the latest domain to attract concerns about high-risk foreign vendors, following debates earlier in the year about drones, surveillance cameras and social media platforms. This highlights the need for organisations to take a risk-based approach to the software and hardware inputs to their business.
About CyberCX Intelligence
CyberCX Intelligence is a uniquely New Zealand and Australian focused capability, with unparalleled visibility into the AUNZ cyber threat landscape. We have the information, access and context to give our partners a decision advantage. Our partners receive:
- Actionable, contextualised intelligence, analysed by experts in AUNZ threat analysis.
- Sector and organisation-specific insights that are relevant and timely.
- High value, low volume artefacts that help their information overload, not add to it.
- A two-way partnership with intelligence designed for your organisation and how you plan to use it.




