Timely reminder to teach users about high-risk file types: Gootloader infections hit Australia

Welcome to the February edition of Cyber Adviser, a monthly readout of insights and expert analysis from the CyberCX Intelligence desk.

Since November 2022, CyberCX has been responding to Gootloader infections in Australian organisations. Gootloader is a malware distribution service linked to pre-ransomware activity. In recent months, the real estate (development and management) and healthcare sector have been most affected. Gootloader payloads have been distributed via a highly successful search-engine optimisation campaign. In the Gootloader infections observed by CyberCX, the infected users were seeking templates related to contracts using Google and Bing. They were directed to fake forum posts. One of the forum users posted a link to the Gootloader ZIP and three other forum users purportedly thanked them for the file. The threat actor almost certainly created similar fake forum posts with different fake document templates.
In the incidents we observed, Endpoint Detection and Response capabilities were key to mitigating Gootloader’s impact. Organisations are also likely to gain some protection through user education, as Gootloader requires manual downloading from an untrusted source and user execution of a high-risk file type.
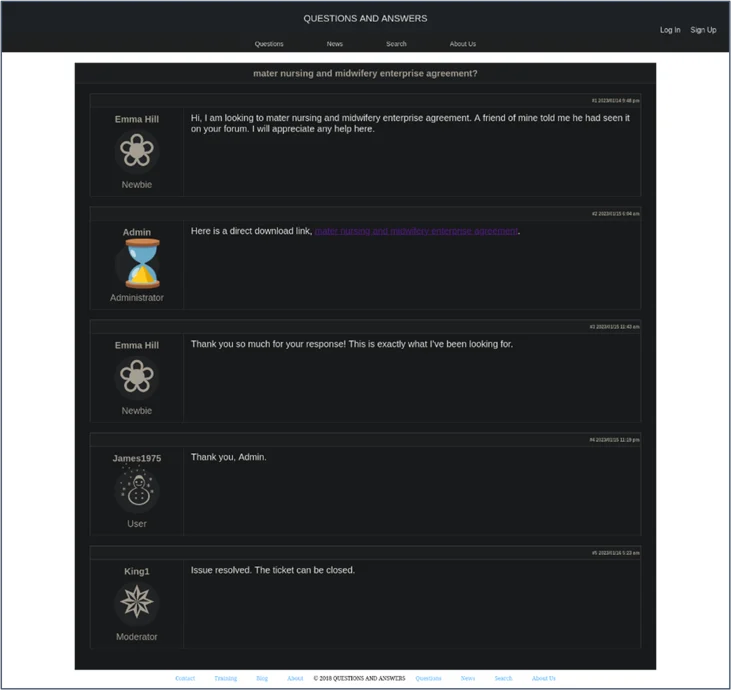
Example of fake forum exchange identified by CyberCX Intelligence
Hive, disrupted: Global law enforcement action against cyber extortion continues
In late January, the US Department of Justice announced that the FBI had covertly infiltrated the Hive ransomware group and disrupted its activities. Hive had a history of targeting AUNZ organisations. The FBI provided Hive decryption keys to more than 300 victims under active attack and more than 1,000 previous victims, reportedly saving victims more than US $130m in ransom demands. Hive’s darknet infrastructure has been taken down and replaced with an FBI seizure notice.

Seizure notice placed on the Hive dedicated leak site (DLS)
While the take-down is likely to cause some disruption to Hive affiliates, we do not assess it will materially reduce the risk of cyber extortion for AUNZ organisations, given the resilience of the cyber extortion economy.
Fighting code with law: The IT managed service provider that took its cyber extortion fight to the New Zealand High Court
Over January, New Zealand healthcare and government organisations continued to face public scrutiny about whether any sensitive records were exposed during a 2022 cyber extortion attack. In November, LockBit claimed to have compromised New Zealand-based IT managed service provider (MSP), Mercury IT, and its downstream clients. In late December, the High Court of New Zealand (HCNZ) granted an application from two impacted organisations, Te Whatu Ora Health New Zealand and the New Zealand Ministry of Justice, to make an order preventing unauthorised use of data stolen by LockBit. The HCNZ prohibited actions including searching, reviewing, disclosing or publishing the stolen data, and also ordered the deletion of any existing copies of the data.
Unfortunately, MSPs are increasingly common targets of cyber extortion attacks. But the case is notable because AUNZ organisations do not commonly seek legal remedies following cyber extortion events. New Zealand courts have suppressed the publication of ransomware-related information, but only in relation to publication and dealings by named defendants rather than the general order made in relation to Mercury IT. CyberCX Intelligence is not aware of a similar case in Australia.
Organisations should consider every tool available to them when responding to cyber extortion incidents. Seeking orders from courts may be helpful in some cases. We judge recourse to the courts may draw additional media and public attention to breached data. Legal orders are highly unlikely to impact on criminal behaviour and may be prohibitively expensive to pursue in multiple jurisdictions, particularly internationally. Recourse to the legal system is most likely to be an effective tool in circumstances when there is a clear legal basis for an order, media interest in the incident is already high and the incident is largely contained to a single country.





