Cyber extortion: Record highs, splintering groups

Welcome to the first edition of Cyber Adviser, a monthly readout of insights and expert analysis from the CyberCX Intelligence desk.
Cyber extortion: Record highs, splintering groups
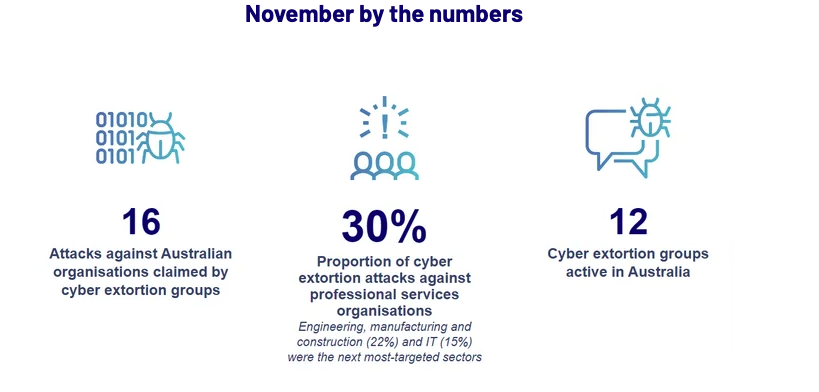
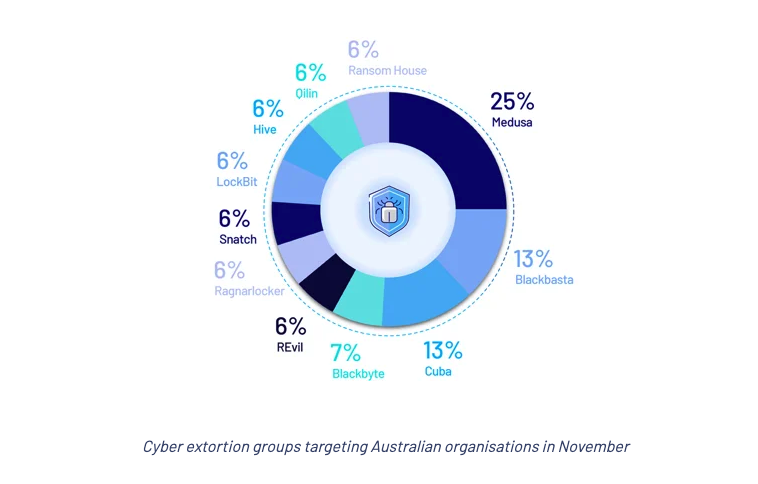
Cyber extortion attacks against Australian organisations increased to the highest level CyberCX Intelligence has observed in 2022. Cyber extortion groups claimed responsibility for attacks against at least 16 Australian organisations. The cyber extortion ecosystem is more volatile and fractured. November activity was split across at least 12 unique cyber extortion actors. This is a significant increase on the number of groups active in previous months.
Why? One explanation is the increasing commoditisation of cyber crime services—from phishing-as-a-service to initial access—which is empowering more and smaller groups to participate in the cyber extortion economy. Another explanation is the Russia-Ukraine war, which has triggered instability and change in how cyber extortion groups target and are organised.
So what? New groups may be less detectable and predictable. They’re also experimenting with new tradecraft. For example, some cyber extortion groups are becoming better at finding and exploiting sensitive personal information to maximise harm to their victims.
Espionage: The pervasive, silent threat
Australia’s terrorism threat level was downgraded from “probable” to “possible” for the first time since 2014. This follows the Australian Security Intelligence Organisation’s announcement in February that espionage and foreign interference have supplanted terrorism as its “principal security concern.”
Why? The change in national threat level in part reflects the government’s reprioritisation of attention and resources to threats to Australian organisations including espionage.
So what? CyberCX Intelligence continues to assess that there’s an increasing likelihood of nation-state espionage targeting in Australia, especially against government, research, energy and defence-adjacent organisations and those that otherwise hold sensitive personal information. Controls that mitigate cyber crime risk, such as phishing detection and prevention and patching known critical vulnerabilities, can also reduce espionage risk.





