April 2023

Welcome to the April edition of Cyber Adviser, a monthly readout of insights and expert analysis from the CyberCX Cyber Intelligence desk.
As the cyber environment continues to rapidly evolve, Cyber Adviser cuts through the noise and gives you visibility of what matters most – all in 5 minutes or less.

End of an era: Law enforcement takes down prolific data leak site, Breach Forums
In March, US authorities announced the arrest of Pompompurin, the creator and primary administrator of BreachForums, a highly active and popular cyber crime community. At the time of its seizure, BreachForums had more than 300,000 registered member accounts. Its popularity likely stemmed from the fact it was accessible on the clear net (so users didn’t need dark web access) and its open registration policy, allowing anyone to sign up.
Over the past 12 months, BreachForums has been a key nexus for cyber crime. The site enabled cyber criminals to host, leak and sell data obtained from breached companies, including during the high-profile Optus extortion attempt in September 2022.
Lower level, open cyber crime communities such as BreachForums are key facilitators of cyber crime and operate as referral platforms for existing threat actors. These communities are substantially more accessible to low-sophistication or prospective cyber criminals, reducing the barrier to entry to the cybercrime ecosystem and acting as gateways into higher level criminal communities.
Despite the takedown, the cyber crime ecosystem is resilient and adaptable. It is almost certain that new communities will establish in the near term to fill the market gap left by BreachForums and to capitalise on displaced members.
opAustralia: a loosely aligned hacktivist operation
In March, a runway exhibition by an Australian brand at the Melbourne Fashion Festival included clothing bearing the text “God walks with me” in Arabic. The use of the Arabic ‘Allah’ (meaning God) prompted a response from a loose network of nationalistic and religiously motivated hacktivist groups operating via Telegram.
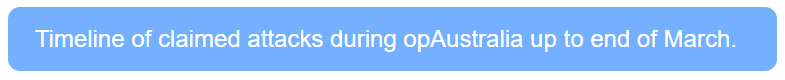
On 17 March, a group of hacktivists initiated “opAustralia”, a campaign of reprisal attacks for having “challenged us Muslim hackers”. Between 17 March and 24 March, opAustralia participants claimed to have targeted at least 80 Australian organisations with DDoS attacks, website defacements and hack and leak operations, focusing on organisations in the transportation, education, government and finance sectors.
Anonymous Sudan 2023, a hacktivist group purportedly originating from its namesake country, joined opAustralia in late March, announcing plans to target Australian higher education, aviation and healthcare organisations. Despite its claims, we assess with moderate confidence that Anonymous Sudan 2023 is a pro-Russia hacktivist actor.
In context of the increasing threat of pro-Russia hacktivism since the start of the Russia-Ukraine war, the opAustralia campaign demonstrates that these hacktivist threats can arise with little warning and will attack organisations with little to no direct connection to national security issues.
While the targeting claimed by Anonymous Sudan 2023 was widespread, the harm caused was minimal. CyberCX Cyber Intelligence assesses that claims made by hacktivists during opAustralia were almost certainly false or overstated. Many hacktivist groups are focussed on publicity and attention – claiming victims can be more important (and easier) than causing lasting damage. This highlights the need for organisations to ensure technical mitigations are up to date, like DDoS protection, but also the importance of reputation management and cyber incident communication strategies.
Teach a man to phish: Caffeine PhaaS platform increases threat actor capability
In February and March, CyberCX observed sophisticated credential phishing attacks impacting organisations in Australia and New Zealand. We assess that this cluster of phishing activity was likely facilitated by the phishing-as-a-service (PhaaS) platform marketed as “Caffeine”.
Caffeine is a subscription platform for cyber criminals. It offers subscribers access to Microsoft-themed phishing pages to validate email addresses and obtains the victim organisation’s banner image, mimicking the behaviour of real Microsoft login pages. It also offers adversary-in-the-middle sessions and multifactor authentication (MFA) capture capabilities, significantly increasing subscribers’ ability to overcome access controls.
CyberCX observed two instances of attempted post-compromise activity we associate with the Caffeine activity cluster. These attempts consisted of efforts to establish persistence, add permissions and facilitate ongoing access to a compromised user’s email account. We assess the threat actor in both cases was likely planning to conduct a Business Email Compromise attack – a popular attack type where the threat actor redirects the victim’s outgoing payments to themselves.
Cybercrime-as-a-service platforms, including PhaaS, improve the scale and effectiveness of cyber criminal operations. Subscription models like Caffeine allow low-level cyber criminals to obtain higher sophistication capabilities. The Caffeine PhaaS has been unavailable through April, however we assess it is likely to resume operations within the next month.
Caffeine and similar PhaaS services also provide users with hardened phishing pages that can evade detection and can capture a victim’s MFA-authorised sessions. These features will almost certainly increase the success rate of successful phishing attempts against Australian and New Zealand organisations.




