Threat Advisory. Lessons learned: Phishing and impersonation campaign targeted Australian organisations through abuse of e-Learning provider

Published by CyberCX Cyber Intelligence on
Key Points
- CyberCX has observed and disrupted a phishing campaign targeting Australian organisations primarily in the government, healthcare, professional services and utilities sectors.
- Between March and June 2022, CyberCX responded to a series of phishing incidents in which an unknown threat actor repeated the following attack chain:
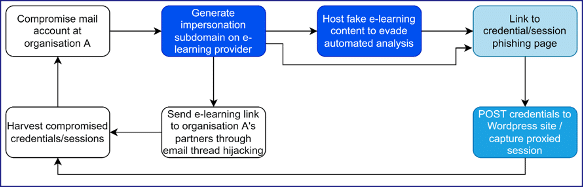
- Gain access to access to Organisation A’s email account
- Register a subdomain with an e-learning provider to impersonate Organisation A
- Host malicious phishing redirects masquerading as e-learning content or shared documents
- Use the compromised email account to send links to the malicious subdomain to Organisation A’s partners through email thread hijacking.
- CyberCX proactively notified affected organisations and advised the e-learning provider of the persistent abuse of its services. Following CyberCX’s notification, the e-learning provider removed malicious infrastructure and interrupted the threat actor’s ability to continue the campaign.
- CyberCX Intelligence has been unable to link this phishing campaign to a specific actor or financial motive, but assesses it is likely an at least moderately-resourced threat actor with sustained intent to target Australian organisations.
Campaign Description
- Between March and June 2022, CyberCX responded to incidents in which a threat actor abused a legitimate e-learning provider to impersonate Australian organisations and to launch phishing attacks against those organisations’ supply chains.
- We assess with moderate confidence that this campaign has been active since at least July 2021.1
- After compromising access to an email account at an organisation, the threat actor registered an account with the e-learning provider which impersonated the compromised organisation’s domain.
- Registration resulted in the e-learning provider generating a subdomain under the control of the threat actor which matched the compromised organisation’s name without relying on a misspelled or otherwise misleading domain.
- On impersonation subdomains, the threat actor hosted malicious phishing redirects hidden in fake e-learning content or shared documents. The threat actor then used email thread hijacking to send links to this fake content to the compromised organisation’s partners.
- Figure 1 represents our assessment of the overall attack.
- In most instances observed by CyberCX, the e-learning content generated by the threat actor masqueraded as a secure document transmission service matching, or similar to, Figure 2.
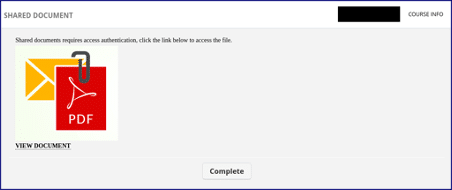
- The “VIEW DOCUMENT” element in Figure 2 contained a hyperlink to second stage phishing infrastructure. Second stage infrastructure observed by CyberCX included:
- Subdomains on temporary web-hosting/web-app development services Glitch (glitch[.]me) and Fleek (fleek[.]co)
- Dynamic DNS subdomains using Duck DNS (duckdns[.]org)
- Generic malicious domains generated by the threat actor.
- CyberCX observed one incident in which malicious links were not exposed until a visitor to the malicious page completed an e-leaning test. We assess that this tactic was likely an attempt to frustrate automated detection of malicious pages.
- Second stage phishing infrastructure observed by CyberCX consisted of credential phishing themed around Adobe Cloud and Microsoft Office 365 login pages. These phishing pages were designed for credential theft.
- Our examination of phishing pages between March and May indicates that credentials entered by victims were sent via POST to PHP-based phishing kits hosted on a separate, legitimate-but-compromised WordPress sites.
- In June 2022, we observed phishing pages containing a man-in-the-middle (MITM) proxy functionality capable of intercepting Two Factor Authentication challenges and stealing session cookies as well as input credentials. CyberCX confirmed the proxy functionality by triggering a MITM phishing page controlled by the threat actor. The proxied login session originated from Europe.
Assessment
- Australia was the most heavily impacted country according to our observations. We also observed targeting of organisations in the US and Greece. Impacted Australian sectors include:
- Government (22%)
- Professional services (22%)
- Healthcare (19%)
- Energy and utilities (19%)
- Construction and engineering (6%)
- Retail and wholesale (4%)
- Media (4%)
- Transportation and logistics (4%)
- We have been unable to identify the threat actor’s ultimate objective. Affected organisations have not been targeted for cyber extortion at elevated rates and we have been unable to connect this threat actor to access being sold on cyber crime forums or the darknet.
- We assess that the campaign was likely largely automated, based on the scale of the campaign and the high incidence of near-identical tradecraft. The threat actor had a high operational cadence – we observed the creation of subdomains at most 24 hours before phishing links were sent from compromised mailboxes.
- Despite the likely automation, the threat actor continued to develop and refine the campaign. We observed more than 20 variations of first and second stage infrastructure indicating the threat actor’s continued resource expenditure to improve and customise phishing lures. This level of ongoing development is consistent with a dedicated threat actor with a sustained interest in Australian organisations.
- We assess that the threat actor abused the online learning provider to generate legitimate-looking domains that were likely to deceive intended victims. The e-learning parent domain is also commonly whitelisted by security products due to its popularity.
CyberCX Response
- Leveraging our visibility across Australian networks, CyberCX Intelligence was able to proactively detect malicious impersonation subdomains created by the threat actor.
- In June, CyberCX Intelligence notified more than 25 Australian organisations that they had been targeted by this threat actor.
- In several instances, CyberCX notifications resulted in the identification of intrusions, including at least one active intrusion. This permitted the organisation to remediate before the threat actor could access systems and proliferate.
- In June, CyberCX shared our findings with the e-learning provider. In July, the e-learning provider removed all known instances of malicious infrastructure and changed their systems to prevent further abuse.
- We assess that these changes are likely to prevent the threat actor from continuing this campaign in its current form.
- However, the threat actor has demonstrated a sustained focus on targeting Australian organisations and is likely to develop a new method to continue its campaign in the short term.
Additional Information
This is a TLP:WHITE version of CyberCX Threat Advisory TA-2022-016, released 15 June 2022. If you have been affected by this campaign and would like access to the full technical report including Indicators of Compromise, please contact us at [email protected].
For additional information, including specifics about the response within your IT environment, please contact [email protected] or your usual CyberCX contact.
If you are not a customer but would like help responding to the subject of this advisory, please contact [email protected].
| CyberCX Reference No# | Date of Advisory |
| CCX-TA-2022-016.1 | 12 July 2022 |
This threat advisory has been prepared by the CyberCX Intelligence Team.
Read more about our practices and insights:
If you need assistance responding to a cyber incident, please contact our investigation and response team here.
Guide to CyberCX Cyber Intelligence reporting language
CyberCX Cyber Intelligence uses probability estimates and confidence indicators to enable readers to take appropriate action based on our intelligence and assessments.
| Probability estimates – reflect our estimate of the likelihood an event or development occurs | ||||||
| Remote chance | Highly unlikely | Unlikely | Real chance | Likely | Highly likely | Almost certain |
| Less than 5% | 5-20% | 20-40% | 40-55% | 55-80% | 80-95% | 95% or higher |
Note, if we are unable to fully assess the likelihood of an event (for example, where information does not exist or is low-quality) we may use language like “may be” or “suggest”.
| Confidence levels – reflect the validity and accuracy of our assessments | ||
| Low confidence | Moderate confidence | High confidence |
| Assessment based on information that is not from a trusted source and/or that our analysts are unable to corroborate. | Assessment based on credible information that is not sufficiently corroborated, or that could be interpreted in various ways. | Assessment based on high-quality information that our analysts can corroborate from multiple, different sources. |
1] Assessment based on open source reporting on a similar attack method. See, e.g., https://cofense.com/blog/simplistic-phish-bypass-gateway/







