
Published by CyberCX Cyber Intelligence on 7 March 2023
CyberCX Intelligence actively monitors the cyber threat landscape for emerging and novel threats to Australian and New Zealand organisations. This Intelligence Update provides situational awareness of cyber attacks attributed to a new and prolific cyber extortion group, calling itself Medusa Team.[1]
Key Points
- CyberCX Intelligence assesses Medusa Team poses a high threat to organisations in Australia, New Zealand and the Pacific region for at least the next three months.
- In January 2023, Medusa Team commenced double extortion operations, including in Australia and the Pacific region.
- Medusa Team has a high operational tempo and wide-ranging targeting pattern, having already impacted the manufacturing, telecommunications, energy, hospitality and professional services sectors.
- CyberCX has identified multiple instances of poor operational security and cryptographic implementation related to this actor.
- Several cyber criminal operations use “Medusa” as part of their branding. We assess with moderate confidence that Medusa Team does not overlap with other threat actors named Medusa, including Medusa Locker, the Medusa Stealer botnet and the Medusa Android trojan.
Medusa Team
We assess Medusa Team poses a high threat to organisations in Australia, New Zealand. In February alone, Medusa Team was the second most frequent cyber extortion group to target organisations in the Pacific region.
- Medusa Team has been active since at least 11 January 2023. At least 20 victims have been listed on its dedicated leak site (DLS) across multiple countries including Australia, Indonesia, Iran, Kenya, Singapore, Tonga and the US.
- Medusa Team engages in double extortion, deploying ransomware to encrypt victim data and exfiltrating and threatening to publish stolen data.

- Medusa Team’s high operational cadence indicates that the group almost certainly comprises at least a small group of experienced threat actors. We assess there is a real chance Medusa Team is a standalone operation with discrete tradecraft and indicators.[2]
- Medusa Team malware is sufficiently distinct and immature to suggest development outside of known actor groups.
- Medusa Team’s DLS and associated websites do not mention affiliate programs often seen with larger cybercrime outfits.
- CyberCX Intelligence can share additional detection, response and mitigation advice with Australian and New Zealand organisations. CyberCX may also be able to assist victims of Medusa Team with recovery of encrypted data.
Social networking
Medusa Team has a dedicated public relations strategy across dark and clear web platforms, likely intended to amplify damage to victims. This may increase the effectiveness of its double extortion threats.
- CyberCX Intelligence has identified several social media and messaging accounts across Telegram and Facebook, as well as a domain, which we assess with moderate confidence are all operated by Medusa Team.
- Medusa Team’s public relations strategy aligns with a trend CyberCX Intelligence has monitored since 2022. Cyber criminals are increasingly using internet platforms like Breach Forums to advertise compromises, likely to increase extortion pressure.
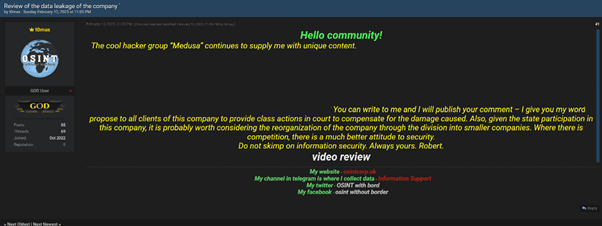
- Medusa Team’s association with a purported cyber security professional, “OSINT without borders”, is likely an attempt to build credibility and is a notable tradecraft development.
We assess with high confidence that “OSINT without borders” is operating as the public relations function of Medusa Team and reports on breaches and republishes stolen data.
- OSINT without borders operates a purported threat intelligence website and is active on criminal forums, including Breach Forums, a popular internet cyber criminal forum and marketplace.
- The Telegram button on the Medusa Team DLS links to a channel called “information support” with a logo comprising a globe and the title “OSINT without borders”.[3]
- A Medusa Team ransom note obtained by CyberCX explicitly links Medusa Team back to OSINT without borders.
- A user on Breach Forums, under the moniker “t0mas”, published a purported review of data they claim to have received from Medusa Team relating to a victim which also appeared on the Medusa Team DLS.
- t0mas uses the same profile picture as the “information support” Telegram channel.
- t0mas’s Breach Forums profile claims to own the “information support” Telegram channel.
- t0mas’s Breach Forums profile claims to own a domain called osintcorp[.]uk.
- t0mas’s Breach Forums profile claims to own a Facebook profile named “Robert Enabler” with the handle @OSINTwithoutborder.
- t0mas’s Breach Forums profile claims to own a Twitter account named “Robert Vroofdown” with the handle @OSINT_with_bord. This Twitter account uses the same profile picture t0mas’s Breach Forums profile and the “information support” Telegram channel. This Twitter account links all of the above profiles and sites to the same individual or group.
- t0mas uses the same profile picture as the “information support” Telegram channel.
- The Twitter button on the Medusa Team DLS links to a Twitter search for “Medusa ransomware” using Onion Twitter.[4]


Technical Analysis
- An analysis of ransomware that CyberCX obtained provides some insight into Medusa Team’s likely tradecraft and key implementation weaknesses.
- The ransomware contains an obfuscated, but hard-coded, ransom note and public encryption key, both of which are unique to each victim. These features mean that the ransomware is compiled per victim, likely after initial access has been achieved. Per-victim compilation means that detection via file hash is highly unlikely.
- The ransomware stops services including security products, databases and virtualisation services before encryption. The list of services Medusa Team ransomware targets appears to have been derived from Ryuk ransomware (attributed to a criminal group tracked as Wizard Spider), however has likely been used in several ransomware strains. Medusa Team ransomware may be detected as Ryuk ransomware by security products.
- The ransomware erases itself after executing, likely to impede analysis and recovery. The ransomware does not contain anti-analysis measures, which makes analysis significantly easier than more complex malware strains.
- The ransomware only encrypts a small portion at the beginning and end of files, irrespective of file size. While this aids faster execution of the malware, it makes forensically recovering data a realistic possibility.
- The ransomware does not make network connections and does not appear to have proliferation capabilities. We assess that Medusa Team likely deployed the ransomware via remote access to system or through an administrative method (e.g. Group Policy Object).
- The ransomware does not exhibit a data exfiltration capability, indicating that data collection and exfiltration is carried out via separate means.
Similar Name, Different Threat Actors
Medusa Locker
We assess that Medusa Team and Medusa Locker are likely not the same cyber extortion operation.[5]
- Medusa Locker is a cyber extortion operation that was active from 2019 until at least July 2022. We assess with low confidence that Medusa Locker was active most recently in November 2022.
- There are key tradecraft and infrastructure differences between Medusa Team and Medusa Locker.
- Medusa Locker’s last DLS post is dated July 2022 and is aesthetically different to Medusa Team’s DLS.[6]
- Medusa Locker has DLS infrastructure that remains active in parallel to Medusa Team’s likely newly-created DLS.
- Medusa Locker’s DLS contains the statement that the threat actor is not applying a name to themselves, whereas Medusa Team’s DLS explicitly provides their name as Medusa Team.
- Medusa Locker has no apparent association to “Osint without borders”, whereas Medusa Team a very strong association, and potential overlap, with Osint without borders.
Medusa DDoS Botnet and Medusa Stealer
We assess that Medusa Team and Medusa Stealer (also known as the Medusa DDoS botnet) are highly likely not the same cyber extortion operation.[7]
- Medusa Stealer is a high-volume cyber criminal operation focused on recruiting infected devices to enable DDoS attacks. It has been active since at least 2015.
- There are key tradecraft and infrastructure differences between Medusa Team and Medusa Stealer.
- While Medusa Stealer operators added a ransomware component to the malware in a January 2023 update, the ransomware appears to function as a single-host locker rather than being used for Big Game Hunting operations.
- The Medusa Stealer ransom note demands a fixed ransom and does not direct victims to a DLS.[8]

- In February 2023, an updated version of the Medusa DDoS botnet emerged, featuring a ransomware module and a Telnet brute-forcer.[9] The encryption method for the ransomware module appears to be broken, displaying a ransom note after files have been deleted.
[1] From time to time CyberCX Intelligence makes threat actor profiles public, if we judge that doing so will benefit our Australian and New Zealand communities. We do this after weighing the risks that publishing threat actor information may influence their tradecraft or operations and the benefits of providing actionable intelligence to cyber defenders.
[2] We make this assessment with medium confidence.
[3] The Telegram channel is https://t[.]me/+yXOcSjVjI9tjM2E0
[4] https://twitter3e4tixl4xyajtrzo62zg5vztmjuricljdp2c5kshju4avyoid.onion/search?q=medusa%20ransomeware&src=typeahead_click
[5] We make this assessment with medium confidence.
[6] The DLS address is http://z6wkgghtoawog5noty5nxulmmt2zs7c3yvwr22v4czbffdoly2kl4uad[.]onion
[7] We make this assessment with medium confidence.
[8] https://blog.cyble.com/2023/02/03/new-medusa-botnet-emerging-via-mirai-botnet-targeting-linux-users/
[9] https://blog.cyble.com/2023/02/03/new-medusa-botnet-emerging-via-mirai-botnet-targeting-linux-users/







